This Configuration Guide shows how to configure a GRE tunnel within an IPsec connection.
Situation
A remote router has several local subnets that need to be addressed from the INSYS Smart Device. An IPsec connection only allows to address one subnet. A GRE connection can be established to more than one subnet, but cannot be encrypted. To be able to establish encrypted connections to more than one subnet, it is possible to route a GRE tunnel through an encrypted IPsec connection.
Solution
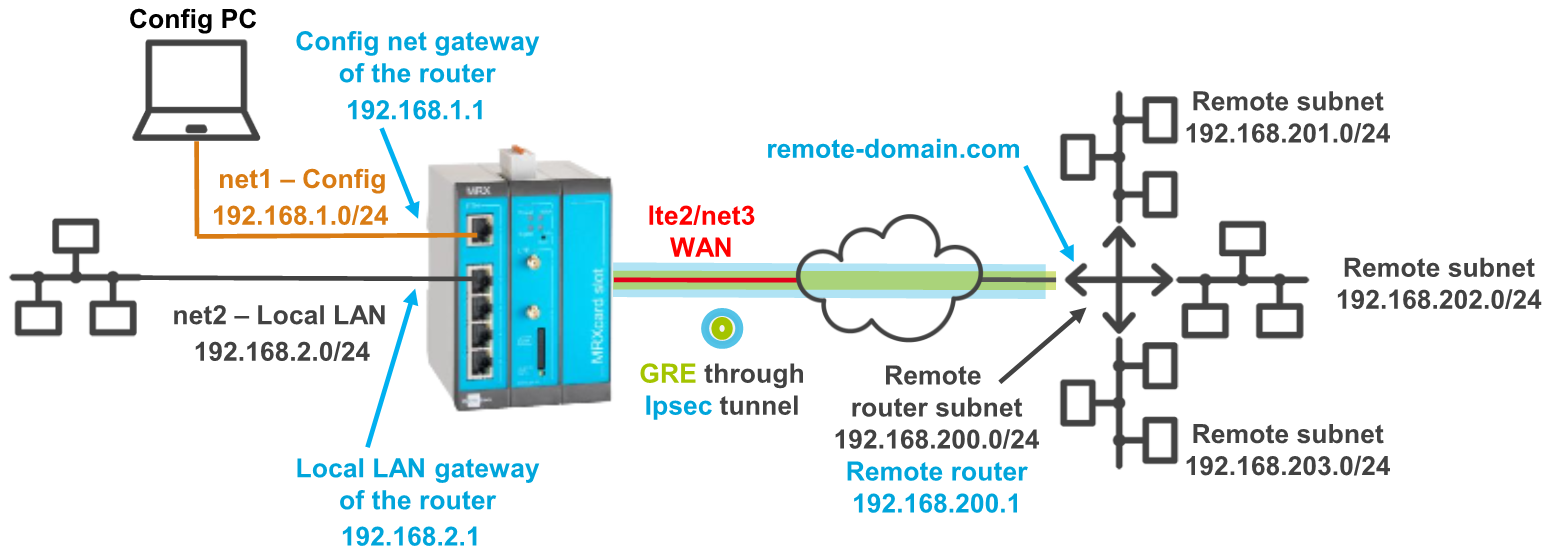
It is prerequisite that you have access to the web interface of the router and the router is configured for a WAN connection using the startup wizard from default settings. It is also prerequisite that the remote router supports GRE via IPsec. The following figure shows the network topology that is used for this example:
-
Open web interface of the router using a browser: 192.168.1.1 [1]
-
In the Interfaces → IPsec menu, add a new IPsec tunnel () and edit it (): [2]
-
Description: IPsec tunnel to remote-domain.com
-
IP address or domain name of remote site: remote-domain.com
-
Local tunnel address: 192.168.2.0
-
Local subnet: 192.168.2.0 / 24
-
Remote subnet: 192.168.200.0 / 24
-
-
Configure authentication and encryption according to the settings of the remote router. [3]
-
Click on Save settings.
-
In the Interfaces → GRE menu, add a new GRE tunnel () and edit it (): [4]
-
Description: GRE tunnel to remote router
-
IP address or domain name of remote site: 192.168.200.1
-
Own IP address: 192.168.2.1
-
Local tunnel address: 10.10.10.10 / 30 [5]
-
GRE key: Enter a GRE key only if the remote router requires this.
-
-
Click on Save settings.
-
In the Routing → Static routes menu, add a new route () and edit it (): [6]
-
Description: GRE route to 192.168.200.0
-
Set after start of: ipsec1
-
Type of the route: network 192.168.200.0 / 24
-
Gateway: interface ipsec1
-
-
Click on Save settings.
-
In the Routing → Static routes menu, add a new route () and edit it (): [7]
-
Description: GRE route to 192.168.201.0
-
Set after start of: gre1
-
Type of the route: network 192.168.201.0 / 24
-
Gateway: interface gre1
-
-
Click on Save settings.
-
Add the next two routes to the remote subnets 192.168.202.0 and 192.168.203.0 accordingly.
-
In the WAN → WAN chains menu, go to the WAN chain entered by the Startup Wizard (wan1), add an interface to the WAN chain () and edit it (). [8]
-
Under Interface, select the IPsec tunnel defined above.
-
Click on Save settings.
-
In the WAN → WAN chains menu, go to the WAN chain entered by the Startup Wizard (wan1), add another interface to the WAN chain () and edit it ().
-
Under Interface, select the GRE tunnel defined above.
-
Click on Save settings.
-
In the Netfilter → IP filter menu, add a new filter rule () and edit it (): [9]
-
Description: IPsec (tunnel establishment)
-
Packet direction: OUTPUT
-
IP version: all
-
Protocol: UDP
-
Output interface: Check the WAN interface used, i.e. lte2 or net3.
-
Destination port: 500
-
-
Click on Save settings.
-
In the Netfilter → IP filter menu, add a new filter rule () and edit it (): [10]
-
Description: IPsec protocol ESP
-
Packet direction: OUTPUT
-
IP version: all
-
Protocol: ESP
-
Output interface: Check the WAN interface used, i.e. lte2 or net3.
-
-
Click on Save settings.
-
In the Netfilter → IP filter menu, add a new filter rule () and edit it (): [11]
-
Description: IPsec UDP Port 4500 (NAT traversal)
-
Packet direction: OUTPUT
-
IP version: all
-
Protocol: UDP
-
Output interface: Check the WAN interface used, i.e. lte2 or net3.
-
Destination port: 4500
-
-
Click on Save settings.
-
In the Netfilter → IP filter menu, add a new filter rule () and edit it (): [9]
-
Description: IPsec (tunnel establishment)
-
Packet direction: INPUT
-
IP version: all
-
Protocol: UDP
-
Input interface: Check the WAN interface used, i.e. lte2 or net3.
-
Destination port: 500
-
-
Click on Save settings.
-
In the Netfilter → IP filter menu, add a new filter rule () and edit it (): [10]
-
Description: IPsec protocol ESP
-
Packet direction: INPUT
-
IP version: all
-
Protocol: ESP
-
Input interface: Check the WAN interface used, i.e. lte2 or net3.
-
-
Click on Save settings.
-
In the Netfilter → IP filter menu, add a new filter rule () and edit it (): [11]
-
Description: IPsec UDP Port 4500 (NAT traversal)
-
Packet direction: INPUT
-
IP version: all
-
Protocol: UDP
-
Input interface: Check the WAN interface used, i.e. lte2 or net3.
-
Destination port: 4500
-
-
Click on Save settings.
-
In the Netfilter → IP filter menu, add a new filter rule () and edit it (): [12]
-
Description: Traffic through the IPsec tunnel sent by the router
-
Packet direction: OUTPUT
-
IP version: all
-
Protocol: all
-
Output interface: ipsec1
-
-
Click on Save settings.
-
In the Netfilter → IP filter menu, add a new filter rule () and edit it (): [13]
-
Description: Traffic through the IPsec tunnel sent to the router
-
Packet direction: INPUT
-
IP version: all
-
Protocol: all
-
Input interface: ipsec1
-
-
Click on Save settings.
-
In the Netfilter → IP filter menu, add a new filter rule () and edit it (): [14]
-
Description: GRE (tunnel establishment)
-
Packet direction: OUTPUT
-
IP version: all
-
Protocol: GRE
-
Output interface: Check the WAN interface used, i.e. lte2 or net3.
-
-
Click on Save settings.
-
In the Netfilter → IP filter menu, add a new filter rule () and edit it (): [14]
-
Description: GRE (tunnel establishment)
-
Packet direction: INPUT
-
IP version: all
-
Protocol: GRE
-
Input interface: Check the WAN interface used, i.e. lte2 or net3.
-
-
Click on Save settings.
-
In the Netfilter → IP filter menu, add a new filter rule () and edit it (): [15]
-
Description: Traffic from the local net through the GRE tunnel
-
Packet direction: FORWARD
-
IP version: all
-
Protocol: all
-
Input interface: net1, net2
-
Output interface: gre1
-
-
Click on Save settings.
-
In the Netfilter → IP filter menu, add a new filter rule () and edit it (): [16]
-
Description: Traffic through the GRE tunnel to the local net
-
Packet direction: FORWARD
-
IP version: all
-
Protocol: all
-
Input interface: gre1
-
Output interface: net1, net2
-
-
Click on Save settings.
-
Activate the profile by clicking the blinking gear in the title bar ().
-
In the Status → System status menu, enter a Refresh cycle of a few seconds and click on OK to see how the WAN chain containing the tunnels is being established.
-
In the Help → Debugging menu, select the Tool PING and enter available IP addresses from the remote subnets under Parameter to verify the connectivity.
We’ve prepared the following ASCII configuration file for adding the filter rules in one go instead of entering them one by one as described in detail above. Copy and paste it to your text editor or download it using the link below. Don’t forget to adjust it to your application if required.
The ASCII configuration file will add all filters as above with both possible WAN interfaces that can be created by the startup wizard, i.e. lte2 and net3.
Refer to Configuration Guide Adding a List Parameter to a Profile Using Lua to see how to apply an ASCII configuration file to a profile.
netfilter.ip_filter.rule.add netfilter.ip_filter.rule[last].rule_active=1 netfilter.ip_filter.rule[last].rule_description=IPsec (tunnel establishment) netfilter.ip_filter.rule[last].rule_direction=output netfilter.ip_filter.rule[last].rule_protocol=udp netfilter.ip_filter.rule[last].rule_output_if=lte2,net3 netfilter.ip_filter.rule[last].rule_dport=500 netfilter.ip_filter.rule[last].rule_ipversion=all netfilter.ip_filter.rule.add netfilter.ip_filter.rule[last].rule_active=1 netfilter.ip_filter.rule[last].rule_description=IPsec protocol ESP netfilter.ip_filter.rule[last].rule_direction=output netfilter.ip_filter.rule[last].rule_protocol=esp netfilter.ip_filter.rule[last].rule_output_if=lte2,net3 netfilter.ip_filter.rule[last].rule_ipversion=all netfilter.ip_filter.rule.add netfilter.ip_filter.rule[last].rule_active=1 netfilter.ip_filter.rule[last].rule_description=IPsec UDP Port 4500 (NAT traversal) netfilter.ip_filter.rule[last].rule_direction=output netfilter.ip_filter.rule[last].rule_protocol=udp netfilter.ip_filter.rule[last].rule_output_if=lte2,net3 netfilter.ip_filter.rule[last].rule_dport=4500 netfilter.ip_filter.rule[last].rule_ipversion=all netfilter.ip_filter.rule.add netfilter.ip_filter.rule[last].rule_active=1 netfilter.ip_filter.rule[last].rule_description=IPsec (tunnel establishment) netfilter.ip_filter.rule[last].rule_direction=input netfilter.ip_filter.rule[last].rule_protocol=udp netfilter.ip_filter.rule[last].rule_input_if=lte2,net3 netfilter.ip_filter.rule[last].rule_dport=500 netfilter.ip_filter.rule[last].rule_ipversion=all netfilter.ip_filter.rule.add netfilter.ip_filter.rule[last].rule_active=1 netfilter.ip_filter.rule[last].rule_description=IPsec protocol ESP netfilter.ip_filter.rule[last].rule_direction=input netfilter.ip_filter.rule[last].rule_protocol=esp netfilter.ip_filter.rule[last].rule_input_if=lte2,net3 netfilter.ip_filter.rule[last].rule_ipversion=all netfilter.ip_filter.rule.add netfilter.ip_filter.rule[last].rule_active=1 netfilter.ip_filter.rule[last].rule_description=IPsec UDP Port 4500 (NAT traversal) netfilter.ip_filter.rule[last].rule_direction=input netfilter.ip_filter.rule[last].rule_protocol=udp netfilter.ip_filter.rule[last].rule_input_if=lte2,net3 netfilter.ip_filter.rule[last].rule_dport=4500 netfilter.ip_filter.rule[last].rule_ipversion=all netfilter.ip_filter.rule.add netfilter.ip_filter.rule[last].rule_active=1 netfilter.ip_filter.rule[last].rule_description=Traffic through the IPsec tunnel sent by the router netfilter.ip_filter.rule[last].rule_direction=output netfilter.ip_filter.rule[last].rule_protocol=all netfilter.ip_filter.rule[last].rule_output_if=ipsec1 netfilter.ip_filter.rule[last].rule_ipversion=all netfilter.ip_filter.rule.add netfilter.ip_filter.rule[last].rule_active=1 netfilter.ip_filter.rule[last].rule_description=Traffic through the IPsec tunnel sent to the router netfilter.ip_filter.rule[last].rule_direction=input netfilter.ip_filter.rule[last].rule_protocol=all netfilter.ip_filter.rule[last].rule_input_if=ipsec1 netfilter.ip_filter.rule[last].rule_ipversion=all netfilter.ip_filter.rule.add netfilter.ip_filter.rule[last].rule_active=1 netfilter.ip_filter.rule[last].rule_description=GRE (tunnel establishment) netfilter.ip_filter.rule[last].rule_direction=output netfilter.ip_filter.rule[last].rule_protocol=gre netfilter.ip_filter.rule[last].rule_output_if=lte2,net3 netfilter.ip_filter.rule[last].rule_ipversion=all netfilter.ip_filter.rule.add netfilter.ip_filter.rule[last].rule_active=1 netfilter.ip_filter.rule[last].rule_description=GRE (tunnel establishment) netfilter.ip_filter.rule[last].rule_direction=input netfilter.ip_filter.rule[last].rule_protocol=gre netfilter.ip_filter.rule[last].rule_input_if=lte2,net3 netfilter.ip_filter.rule[last].rule_ipversion=all netfilter.ip_filter.rule.add netfilter.ip_filter.rule[last].rule_active=1 netfilter.ip_filter.rule[last].rule_description=Traffic from the local net through the GRE tunnel netfilter.ip_filter.rule[last].rule_direction=forward netfilter.ip_filter.rule[last].rule_protocol=all netfilter.ip_filter.rule[last].rule_input_if=net1,net2 netfilter.ip_filter.rule[last].rule_output_if=gre1 netfilter.ip_filter.rule[last].rule_ipversion=all netfilter.ip_filter.rule.add netfilter.ip_filter.rule[last].rule_active=1 netfilter.ip_filter.rule[last].rule_description=Traffic through the GRE tunnel to the local net netfilter.ip_filter.rule[last].rule_direction=forward netfilter.ip_filter.rule[last].rule_protocol=all netfilter.ip_filter.rule[last].rule_input_if=gre1 netfilter.ip_filter.rule[last].rule_output_if=net1,net2 netfilter.ip_filter.rule[last].rule_ipversion=all
Troubleshooting
-
You may disable the netfilters in the Netfilter → IP filter menu temporarily to find out if wrong filter settings are the cause for connection problems.
Back to the Configuration Guides for icom OS Smart Devices
Back to overview